Security Overview
- The QosCosGrid stack relies on X.509 Public Key Infrastructure (proxy certificates) which is de facto standard authentication mechanism in grid environments.
- All communication is secured using HTTPG/HTTPS protocols.
- Only one service (QCG-Computing) must be started with root privileges. However it adheres privilege separation model (similar to OpenSSH), thus actually only a very small amount of code is running with root privileges. Moreover most of the operations that may have external effect (job submission, stage-in/stage-out operations) are performed as target local user so even breaking the service would not give attacker any more privileges that he already has.
- Any authorization decision is based on provided credentials, not the trust relationship between components.
- The QosCosGrid stack operation model requires static accounts instead of mapping user credential to a one of pool account (which later might be reused by some other user) thus preventing one user from storing malicious content.
Architecture
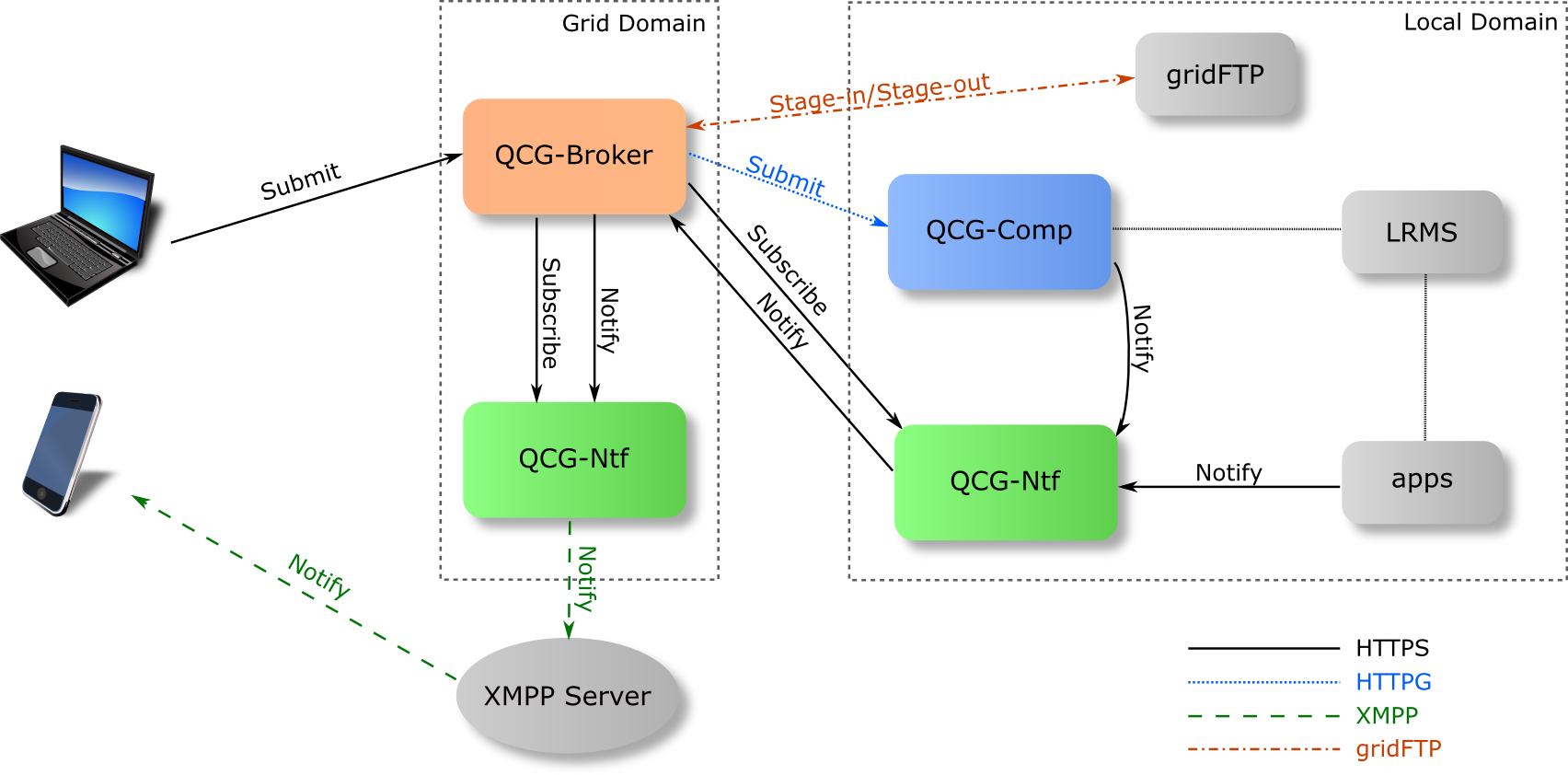
Download in other formats:
 (218.6 KB) -
added by bartek 12 years ago.
(218.6 KB) -
added by bartek 12 years ago.

